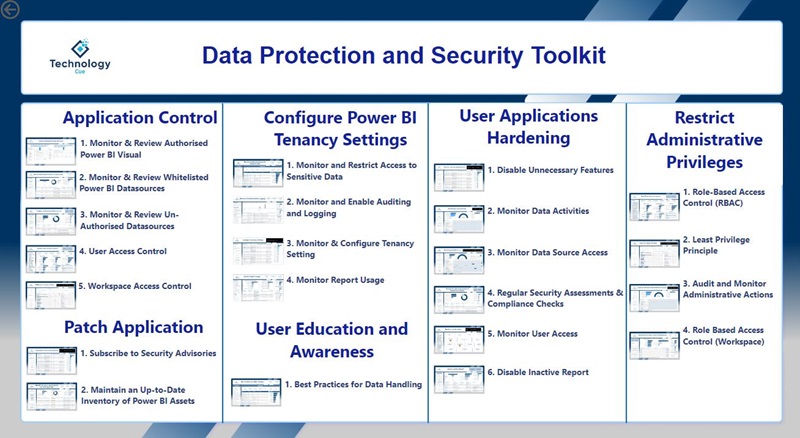
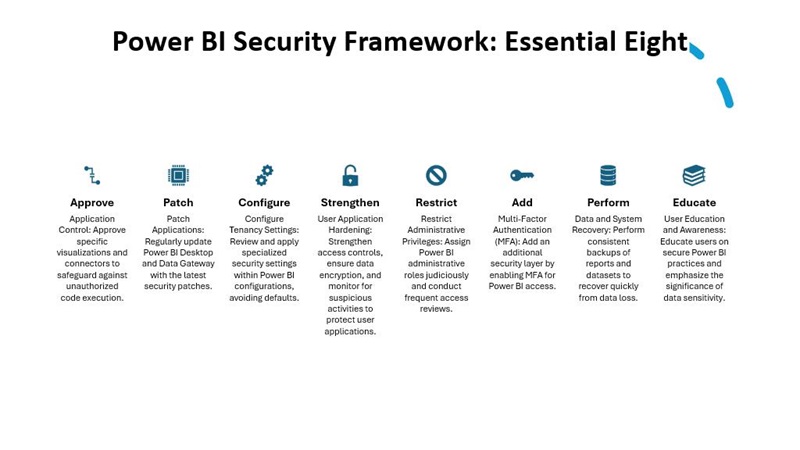
The security blueprint for Power BI emphasizes eight essential protocols:
application control, patch application, configure Power BI tenancy settings, user applications hardening, restrict administrative privileges, multi-factor authentication, recover data and system availability, user education and awareness. These strategies are designed to create a robust defense against cyber threats, safeguarding sensitive data within Power BI’s environment.